Making remote desktop secure starts with choosing a proper remote desktop solution over RDP and VPN, and following these security best practices.
In recent years, attempts to bypass the security of a network via remote desktop have more than tripled. It is important to ensure that your remote desktop connections are safe and do not compromise the security of the rest of your system. Are you aware of the ways that you can guarantee that your use of such tools is safe?
Below, we have detailed information on how you can connect to a remote computer safely. We have also collected tips and advice on how to ensure that your organization has protection from such malicious actors. So, read on and apply the learning to your organization.
What is Remote Desktop Security?
Remote desktop security refers to the measures and protocols put in place to protect remote desktop connections from unauthorized access, data breaches, and other cyber threats. As remote desktop software allows users to connect to and control a computer from a remote location, ensuring the security of these connections is crucial to prevent malicious actors from exploiting vulnerabilities.
Key Aspects of Remote Desktop Security
Encryption: Encrypting the data transmitted between the remote and local machines ensures that even if the data is intercepted, it cannot be read without the encryption key. This protects sensitive information from being exposed.
Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security by requiring users to provide two or more verification factors to gain access to the remote desktop. This reduces the risk of unauthorized access even if login credentials are compromised.
Access Controls: Setting up strict access controls ensures that only authorized users can access the remote desktop. This includes setting user permissions and roles, and regularly reviewing and updating access lists.
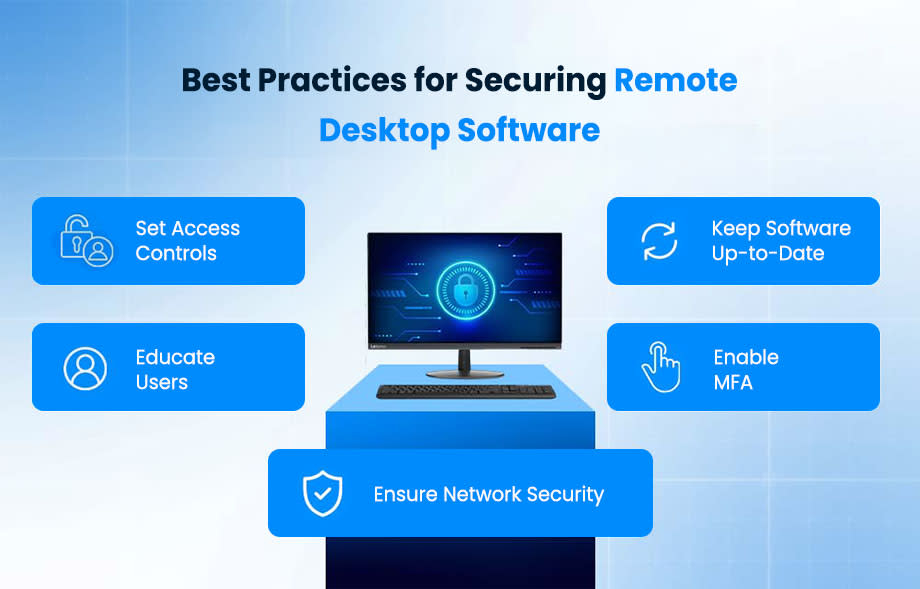
Network Security: Protecting the network on which remote desktops operate is essential. This includes using firewalls and intrusion detection systems to monitor and control incoming and outgoing network traffic.
Regular Updates and Patch Management: Keeping remote desktop software and all connected systems up-to-date with the latest security patches and updates helps protect against known vulnerabilities and exploits.
User Training: Educating users about the best practices for remote desktop security, such as recognizing phishing attempts and using strong, unique passwords, helps minimize human-related security risks.
By implementing these measures, organizations can significantly enhance their remote desktop security, ensuring that their remote connections are as secure as possible.
Top Security Concerns in Remote Desktop Connections
While remote desktop solutions enhance flexibility and productivity, they can also introduce security risks if not properly managed. Here are some of the most common vulnerabilities:
Weak passwords: Simple or reused passwords make it easier for attackers to gain unauthorized access to remote systems.
Session hijacking: Cybercriminals can intercept active remote desktop sessions, taking control of the connection.
Malware & ransomware attack: Remote desktop connections can be exploited to deliver malware or encrypt critical files for ransom.
Brute-force attacks: Hackers use automated tools to guess login credentials and gain access to unprotected remote desktops.
Unpatched software vulnerabilities: Outdated operating systems and applications can contain security flaws that attackers exploit.
Lack of multi-factor authentication (MFA): Without MFA, compromised passwords alone can allow unauthorized access to sensitive systems.
Implementing strong security measures, such as encryption, access controls, and MFA, can help mitigate these risks and protect remote desktop connections from cyber threats.
Remote Desktop Security: Effective Strategies for Maximum Protection
There are specific things that you can do to ensure that your connection remains secure. When wondering how to secure remote access, the following is a list to help you check off each one.
Strong passwords – Force users to only have passwords if they fit a set of criteria. This may be both capital and non-capital letters, with at least one number and one other character.
Set up two-factor authentication – Make sure that people need to confirm their identity via a secondary method on top of their password. This may need their phone or could occur via another method if you have the technology.
Keep your software up-to-date – Ensure that all computers, as well as the systems themselves, are running the latest versions of the operating system. This includes installing any recent security updates to make sure that recent breaches are fixed.
Enable access management – Ensure that you have the policies in place to guarantee that the users accessing your system are the right ones.
Remote Desktop, RDP, or VPN: Which Is More Secure?
Many organizations use remote desktop protocol (RDP) or virtual private networks (VPN) for day-to-day work. However, a remote access solution, like Splashtop, is far more secure than RDP and VPNs, making Splashtop a better alternative to RDP/VPN.
RDP Access
First of all, RDP is not a new piece of technology. When it was first created, people used RDP if they needed to access a system’s computers without needing to physically be in the same room as them.
As such, IT managers made use of RDP to perform their daily tasks with the least discomfort. They could even perform many maintenance roles from a dedicated computer in an IT room or similar.
As network systems matured, it became obvious that such a system was open to abuse by malicious individuals. As such, IT staff started to add more methods of protecting it such as using firewalls or permission lists on the network, making them harder to manage and keep up-to-date.
VPN
VPN is not a new tool. It has its own flaws that are like those that you will find with an RDP, and its age means that they have been around for a long time.
In short, you need to be careful if you want to enable an employee to use a VPN to gain access to your internal system. This is because you have no way of knowing whether their system is safe or not in the first place.
Access security is only as strong as its weakest link, and if you have no control over one of those links, then it will forever be weak.
On top of this, you need to assume that the IT department has configured a VPN correctly. While every effort will be made to ensure that the VPN is secure, mistakes do happen and you cannot always have the assurance that it will keep people out.
Secure Remote Access Software
If you use a piece of secure remote desktop software, you can protect yourself from dangers more readily. A dedicated tool can work alongside your existing systems and is more likely to contain its own methods of securing a network.
Is Remote Desktop Software Secure?
Yes. While there are many secure remote access solutions available on the market, some are better than others. We recommend Splashtop remote desktop software. This piece of technology is one of the most secure on the market.
Key Security Features of Splashtop Remote Desktop Software
You should be aware that compared to VPN and RDP, Splashtop has many features that exist to keep you safe. These include:
App security – All remote sessions through the dedicated app receive advanced protection. This occurs via transport layer security, including TLS 1.2.
Encrypted remote connections – Splashtop’s remote desktop software uses advanced 256-bit AES encryption. This helps to keep any data transfer secure.
You can have the assurance that nobody can spy on the information and files that you access during a remote session.
Two-factor authentication – The Splashtop platform demands that you confirm who you are before logging in. This ensures that the correct person is connecting to the remote desktop at any time.
Device authentication – Before using the remote desktop software, you must register a specific device (or devices) that has access. If a different device attempts to connect, the device must be authenticated by the user first.
Discover How Splashtop's Secure Remote Desktop Solution: Try it for Free Today!
At this point, you should clearly understand how to secure your remote desktop solution effectively. With Splashtop, you get one of the most reliable protections available in the market today. Learn more about Splashtop security.
Start a free trial of Splashtop and experience seamless access to your computers from anywhere, all while benefiting from a remote desktop solution that prioritizes your security.






