Le Patch Tuesday d'août 2025 de Microsoft inclut des correctifs pour 107 vulnérabilités sur Windows, Office, SQL Server, Exchange, Azure, et plus encore. La version de ce mois-ci comprend :
1 zero-day divulgué publiquement
CVE-2025-53779 – une vulnérabilité Windows Kerberos qui pourrait permettre à un attaquant d'escalader les privilèges à un administrateur de domaine.
13 vulnérabilités critiques :
9 failles d'exécution de code à distance
3 problèmes de divulgation d'informations
1 vulnérabilité d'élévation de privilèges
Répartition par type de vulnérabilité :
44 élévations de privilèges
35 exécutions de code à distance
18 divulgations d'informations
9 usurpations
4 Déni de service
Points forts du patch Microsoft
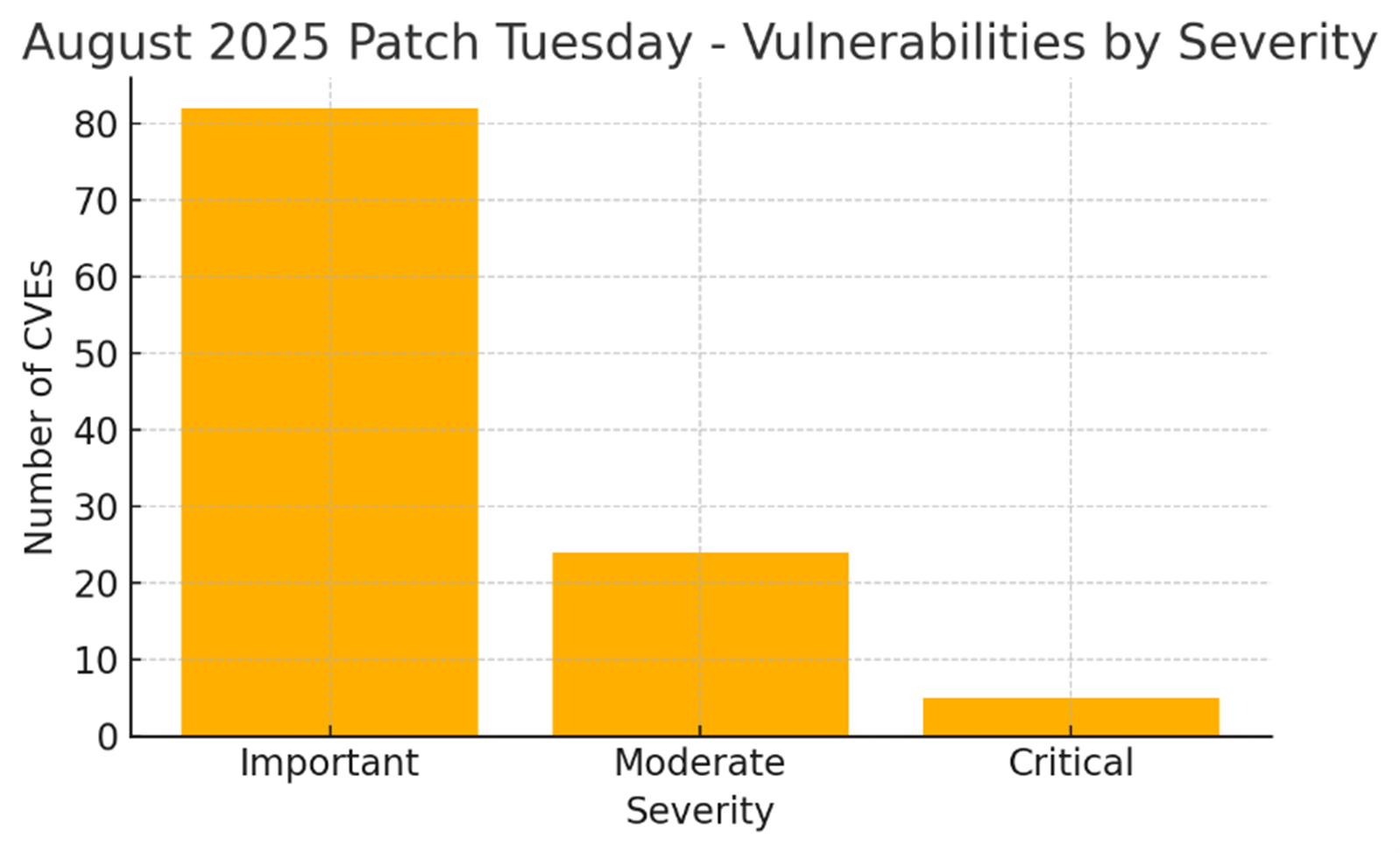
Cette version se concentre fortement sur l'escalade de privilèges et les failles RCE, en particulier dans l'infrastructure centrale de Windows et les services connectés au cloud. Microsoft a également signalé plusieurs vulnérabilités comme étant plus susceptibles d'être exploitées, augmentant l'urgence d'un correctif rapide.
Le Patch Tuesday de ce mois corrige un zero-day divulgué publiquement dans Microsoft SQL Server. Le zero-day divulgué publiquement est :
CVE-2025-53779 - Vulnérabilité d'élévation de privilèges Windows Kerberos
Microsoft corrige une faille dans Windows Kerberos qui permet à un attaquant authentifié d'obtenir des privilèges d'administrateur de domaine.
« La traversée de chemin relatif dans Windows Kerberos permet à un attaquant autorisé d'élever ses privilèges sur un réseau, » explique Microsoft.
Microsoft indique qu'un attaquant aurait besoin d'avoir un accès élevé aux attributs dMSA suivants pour exploiter la faille :
msds-groupMSAMembership: Cet attribut permet à l'utilisateur d'utiliser le dMSA.
msds-ManagedAccountPrecededByLink: L'attaquant a besoin d'un accès en écriture à cet attribut, ce qui lui permet de spécifier un utilisateur pour lequel le dMSA peut agir.
Mises à jour de sécurité tierces à noter
Plusieurs fournisseurs non-Microsoft ont publié des mises à jour importantes autour de ce cycle de Patch Tuesday. Ces correctifs traitent des failles activement exploitées et devraient être inclus dans votre plan de réponse. Les fournisseurs qui ont publié des correctifs incluent :
7-Zip a publié une mise à jour de sécurité pour une faille de traversée de chemin qui pourrait mener à une RCE.
Adobe a publié des mises à jour d'urgence pour les zero-days d'AEM Forms après la publication de PoCs.
Cisco a publié des correctifs pour WebEx et Identity Services Engine.
Fortinet a publié des mises à jour de sécurité aujourd'hui pour plusieurs produits, y compris FortiOS, FortiManager, FortiSandbox et FortiProxy.
Google a publié des mises à jour de sécurité pour Android qui corrigent deux vulnérabilités Qualcomm activement exploitées.
Microsoft a averti d'une faille dans Microsoft Exchange suivie sous le nom CVE-2025-53786 qui pourrait être utilisée pour détourner des environnements cloud.
Proton a corrigé un bug dans sa nouvelle application Authenticator pour iOS qui enregistrait les secrets TOTP sensibles des utilisateurs en texte clair.
SAP a publié les mises à jour de sécurité de juillet pour plusieurs produits, y compris de nombreuses vulnérabilités avec une note de 9,9.
Trend Micro a publié un « outil de correction » pour une vulnérabilité d'exécution de code à distance activement exploitée dans Apex One. Les mises à jour de sécurité complètes viendront à une date ultérieure.
WinRAR a publié une mise à jour de sécurité à la fin de juillet pour un bug de traversée de chemin activement exploité qui pourrait mener à une exécution de code à distance.
Splashtop AEM prend en charge le patching en temps réel pour de nombreuses applications tierces. Les mises à jour comme celles d'Adobe, WinRAR et 7-Zip peuvent être déployées automatiquement en utilisant les politiques de Splashtop AEM, réduisant le temps d'exposition sans effort manuel.
Quels correctifs prioriser en premier
Avec 107 vulnérabilités ce mois-ci, il est important de concentrer vos efforts de correction sur celles présentant le plus grand risque d'exploitation. Les conseils de Microsoft et les notes CVSS aident à identifier ce qui nécessite une attention urgente.
Sur la base des scores CVSS, de la divulgation publique et de la probabilité d'exploitation, les organisations devraient prioriser les éléments suivants :
Corriger immédiatement (Priorité la plus élevée)
CVE-2025-53779
Type: Élévation de privilèges
CVSS : 7,2
Pourquoi c'est important: Zero-day divulgué publiquement dans Windows Kerberos. Peut être utilisé pour obtenir des privilèges d'administrateur de domaine. Corrigez tous les contrôleurs de domaine sans délai.
CVE-2025-50165 – Composant graphique Microsoft (CVSS 9.8, RCE)
CVE-2025-53766 – Windows GDI+ (CVSS 9.8, RCE)
CVE-2025-53792 – Azure Portal (CVSS 9.1, escalade de privilèges)
CVE-2025-50171 – bureau à distance Chrome Server (CVSS 9.1, RCE basé sur le réseau)
CVE-2025-53778 – Windows NTLM (CVSS 8.8, exploitation plus probable)
Ces vulnérabilités affectent des services exposés à Internet ou des services centraux comme RDP, Azure et les systèmes d'authentification Windows. L'exploitation de l'une d'entre elles pourrait permettre aux attaquants d'obtenir un accès privilégié ou de se déplacer latéralement dans votre environnement.
Corrigez dans les 72 heures (Haute priorité)
Vulnérabilités SQL Server – par exemple, CVE-2025-24999, CVE-2025-49758, CVE-2025-53727 (CVSS 8.8)
Microsoft Message Queuing – CVE-2025-53143 à CVE-2025-53145 (CVSS 8.8, RCE)
CVE-2025-53786 – Exchange Server (CVSS 8.0, exploitation plus probable)
Windows RRAS – Plusieurs CVE notés CVSS 8.0+
Ceux-ci affectent des services de grande valeur souvent ciblés dans des scénarios d'accès initial ou de mouvement latéral.
Corriger dans 1 à 2 semaines (Priorité moyenne)
Win32K, Hyper-V, LSASS, DirectX – CVSS 7.x
Vulnérabilités des macros Office et de l'analyse des documents – exploitables via le phishing
Celles-ci sont significatives mais nécessitent généralement une interaction utilisateur ou un accès existant.
Patch dans le cycle régulier (Priorité inférieure)
Failles de moindre gravité dans Office, Visio, PowerPoint
CVEs dans Edge pour Android avec des scores CVSS inférieurs à 7.0
Ceux-ci présentent un risque moins immédiat et peuvent être traités dans le cadre des flux de travail de mise à jour standard.
Comment Splashtop AEM Peut Aider
La mise à jour d'août souligne comment les vulnérabilités évoluant rapidement (comme le zero-day Kerberos et les failles à haut risque dans RDP, NTLM et Azure) nécessitent plus qu'une simple routine de patching mensuelle. Splashtop AEM offre aux équipes TI la flexibilité et la rapidité pour réagir en temps réel, sans perturber les opérations.
Splashtop AEM offre :
Patching en temps réel des OS et des applications sur Windows, macOS et les principaux logiciels tiers
Informations basées sur CVE pour que vous puissiez filtrer, prioriser et corriger en fonction du risque réel
Politiques de patch automatisées pour éliminer le travail manuel répétitif
Contrôle de déploiement basé sur des anneaux pour des déploiements plus sûrs
Tableaux de bord en direct pour suivre le statut des correctifs, les échecs et la conformité en un seul endroit
Fonctionne avec votre pile existante
Que vous utilisiez Microsoft Intune, un RMM traditionnel, ou aucun outil de patching, Splashtop AEM s'intègre parfaitement :
Utilisez-vous Intune ? Splashtop AEM améliore Intune en ajoutant des correctifs en temps réel, un support tiers plus large et une visibilité plus approfondie.
Utilisez-vous un RMM ? Splashtop AEM offre un patching plus rapide, une configuration plus facile et une empreinte plus légère.
Patch encore manuellement ? Automatisez les mises à jour dans votre environnement et libérez du temps précieux.
Splashtop AEM vous aide à rester protégé sans ajouter de complexité. C'est le patching tel qu'il devrait être : rapide, fiable et entièrement sous votre contrôle.
Commencez Votre Essai Gratuit de Splashtop AEM
Patch Tuesday ne doit pas signifier des nuits tardives, des feuilles de calcul et des réactions précipitées.
Avec Splashtop AEM, vous pouvez :
Corriger les vulnérabilités dès qu'elles sont divulguées (y compris les zero-days comme CVE-2025-53779)
Automatisez les mises à jour du système d'exploitation et des tiers sur l'ensemble de votre flotte
Éliminez les angles morts avec une visibilité et des rapports en temps réel
Commencez dès aujourd'hui et prenez le contrôle de votre patching !




