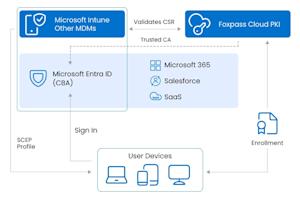
As organizations adopt certificate-based authentication to strengthen Zero Trust initiatives, many begin with Microsoft Cloud PKI to issue certificates to Intune-enrolled devices. It's a streamlined, Microsoft-native approach for issuing certificates across Windows, macOS, iOS, and Android using Intune certificate profiles.
However, most real-world environments extend far beyond Intune. IT teams routinely support Wi-Fi controllers, firewalls, switches, VPN appliances, RADIUS servers, Linux endpoints, IoT systems, Chromebooks, servers, SaaS workloads, and internal application services. Many also use multiple MDMs, especially in environments with macOS or iOS fleets. And nearly all organizations accommodate unmanaged, BYOD, contractor, and guest devices. These system cannot enroll in Intune and therefore cannot receive certificates from Microsoft Cloud PKI. As organizations expand certificate-based access to their networks, applications, and infrastructure, this gap becomes increasingly difficult to bridge without a broader, more flexible PKI.
This is where Foxpass comes in. Foxpass Cloud PKI offers a more flexible, scalable, and complete approach to certificate-based security with coverage for everything inside and outside Intune.
In this blog, we’ll cover what Microsoft Cloud PKI is designed to do, where organizations commonly hit gaps, how Foxpass fills those gaps with a more flexible, infrastructure-wide PKI, and why Foxpass is the most complete alternative for teams who need secure certificate deployment everywhere — not just in Intune.
What Is Microsoft Cloud PKI?
Microsoft Cloud PKI is a cloud-hosted certificate authority designed specifically for Intune-based certificate issuance. It is included with the Microsoft Intune Suite or available as an a-la-carte add-on, and it removes the need to maintain on-premises certificate authorities (AD CS) or the legacy NDES connector while simplifying certificate deployment for devices using Intune-managed certificate workflows. It issues certificates through Intune SCEP and PFX profiles, validates requests through Intune's device management pipeline, and maintains revocation and lifecycle controls appropriate for Intune-bound certificates. This scope is intentional and ensures a simple, secure, end-to-end certificate experience for devices already participating in Intune management.
This makes Microsoft Cloud PKI ideal for organizations fully invested in Intune device management. But that's also the key limitation.
Limitations of Microsoft Cloud PKI
Microsoft Cloud PKI works well for Intune-enrolled endpoints but doesn't address certificate needs across the rest of the network. Below are the limitations most IT teams encounter.
1. Intune-only device enrollment
Microsoft Cloud PKI issues certificates only to devices that are enrolled in Intune and can receive Intune SCEP or PFX profiles. Because Cloud PKI is intentionally scoped to Intune's managed device model, it does not provide a path for certificates to be issued to devices outside Intune — such as BYOD, contractor, guest, or infrastructure devices. As a result, organizations often see coverage gaps when extending certificate-based access to users or systems that sit outside the Intune management boundary.
2. No built-in RADIUS server
Microsoft Cloud PKI does not include a RADIUS service. Organizations implementing certificate-based Wi-Fi (EAP-TLS) or VPN authentication still need a separate RADIUS solution to handle authentication, identity integration, access policies, and network enforcement across their existing infrastructure.
3. No support for CSR or API-based certificate workflows
Microsoft Cloud PKI does not provide CSR upload, API-based certificate issuance, ACME, or SCEP enrollment for devices outside Intune. Because certification workflows are intentionally tied to Intune's managed-device model, there is no enrollment path for servers, microservices, load balancers, appliances, or network infrastructure. This is why many organizations extend or replace Microsoft Cloud PKI with a comprehensive PKI that can serve these additional systems.
4. Limited support for hybrid and BYOD environments
Most organizations operate with mixed MDM environments, macOS fleets managed by Jamf/Iru (Kandji), contractors and external partners, and unmanaged devices needing Wi-Fi access. Microsoft Cloud PKI cannot issue certificates to these devices.
These limitations can create real operational challenges, particularly for teams managing diverse user groups or implementing a zero-trust security model. Organizations looking for a more complete, flexible solution should consider an alternative that goes beyond Intune and fills these functional gaps. Foxpass is built to do exactly that.
Meet Foxpass: The Ideal Microsoft Cloud PKI Alternative
Foxpass Cloud PKI is a cloud-native certificate authority designed to operate across the full range of devices and systems found in modern environments. It supports certificate issuance not only for traditional endpoints, but also for network gear, security appliances, servers, and internal services. The same PKI can be used for Wi-Fi (EAP-TLS), VPN access, NAC deployments, and even for IoT, BYOD, and other unmanaged devices. Foxpass supports SCEP across any SCEP-capable MDM — including Intune, Jamf, Iru (Kandji), Workspace ONE, and Addigy — and it also supports traditional PKI workflows like CSR submission and manual certificate enrollment. For devices that sit outside an MDM entirely, Foxpass offers straightforward BYOD certificate installers to simplify certificate onboarding. Identity synchronization is available with Entra ID, Google Workspace, Okta, OneLogin, and other providers, enabling unified policy enforcement across a broad range of user and device identities.
Foxpass Cloud RADIUS
Beyond certificate issuance, Foxpass provides a fully managed Cloud RADIUS service that is purpose-built to work seamlessly with Foxpass Cloud PKI. Together, they create a unified, end-to-end certificate-based authentication workflow for Wi-Fi and VPN. The service supports EAP-TLS for certificate-based access, EAP-TTLS and PEAP for credential-based methods, and RadSec for transporting RADIUS traffic over secure, TLS-encrypted channels. Foxpass works with widely used Wi-Fi and VPN infrastructure such as Cisco, Aruba, Meraki, Fortinet, and Ubiquiti/UniFi, enabling organizations to strengthen network authentication without overhauling their existing hardware. Because the RADIUS service is cloud-hosted with high availability, IT teams do not need to deploy or maintain on-prem RADIUS servers. Identity and group memberships flow directly from your identity provider, and policies can be applied consistently across all devices, whether they are managed through an MDM, enrolled via SCEP, or onboarded through the Foxpass BYOD installer.
By combining Foxpass Cloud PKI and Cloud RADIUS into a cohesive platform, Foxpass delivers a more complete and scalable alternative to Microsoft Cloud PKI. It’s designed for today’s dynamic IT environments, not just Microsoft-managed ones.
Foxpass vs Microsoft Cloud PKI: Feature Comparison
When evaluating Microsoft Cloud PKI and Foxpass, their differing scopes become apparent. Microsoft Cloud PKI focuses on certificate issuance to Intune-managed devices, offering a clean, integrated experience within that ecosystem. Foxpass, by contrast, supports certificate-based security across your entire environment — including infrastructure devices, mixed-platform fleets, unmanaged endpoints, and systems that require RADIUS-based authentication — providing the broader coverage and scalability many organizations need.
Below is a side-by-side comparison of key features:
Feature | Microsoft Cloud PKI | Foxpass Cloud PKI |
Certificate enrollment | Intune SCEP/PFX only | SCEP (any MDM), CSR, manual workflows, BYOD installer |
Device support | Intune-managed endpoints | Any device: endpoints, servers, infra, IoT, BYOD |
MDM compatability | Intune only | Any SCEP-capable MDM |
RADIUS support | Not included | Built-in Cloud RADIUS with EAP-TLS, EAP-TTLS, PEAP, and RadSec |
Identity integrations | Entra ID via Intune | Entra ID, Okta, Google, OneLogin, and more |
Platform compatibility | Windows, macOS, iOS, Android (Intune-enrolled only) | Windows, macOS, iOS, Android, Chromebook, Linux |
Pricing flexibility | Requires Intune Suite or add-on license | Available as standalone PKI, or included with RADIUS Advanced licensing, no Intune dependency |
Foxpass delivers on the core certificate lifecycle needs while expanding support to unmanaged devices, diverse identity providers, and direct network access control. Organizations that want secure, scalable authentication without being locked into a single device management platform will benefit from Foxpass’s flexibility and ease of deployment.
If your organization is also exploring certificate-based authentication for Entra ID, you may find our guide on How to Configure Microsoft Entra CBA Using Foxpass Cloud PKI helpful. It walks through the setup process and explains how Foxpass-issued certificates integrate cleanly with Entra CBA workflows.
Use Cases Where Foxpass Shines
Foxpass is built to meet the real-world needs of modern IT teams. Its flexibility and built-in network integration make it the ideal solution for organizations that need to secure access across a wide range of devices and environments. Here are some of the most common use cases where Foxpass outperforms Microsoft Cloud PKI:
1. Certificate-based Wi-Fi authentication
Foxpass enables secure, certificate-based authentication for Wi-Fi networks using 802.1x with EAP-TLS. It works seamlessly with access points and network hardware from leading vendors like Cisco, Aruba, Meraki, and Ubiquiti. With Foxpass Cloud RADIUS, there's no need to deploy and maintain your own RADIUS infrastructure.
2. BYOD and unmanaged device enrollment
Unlike Microsoft Cloud PKI, which only supports Intune-enrolled devices, Foxpass makes it easy to issue certificates to any device. Whether it’s a personal laptop, a contractor’s phone, or a Chromebook used in a school setting, Foxpass supports secure onboarding without compromising control.
3. Secure VPN access
Foxpass certificates can be used to authenticate VPN clients across various platforms. IT teams can enforce certificate-based access for remote users, ensuring that only trusted devices can establish VPN connections, without relying on passwords or user enrollment in Intune.
4. Zero-trust identity and network access
Foxpass supports real-time syncing with identity providers like Entra ID and Okta, allowing organizations to enforce access policies based on both user and device identity. When combined with certificate-based authentication and Cloud RADIUS, Foxpass supports a true zero-trust approach across both network and identity layers.
These use cases reflect the growing need for secure, scalable access solutions that go beyond Microsoft’s ecosystem. With Foxpass, organizations can simplify operations, reduce risk, and improve user experience across every environment they manage.
Ready to Replace or Extend Microsoft Cloud PKI? Try Foxpass
Microsoft Cloud PKI may be a convenient option for organizations already deep in the Intune ecosystem, but it falls short when flexibility, broader device support, and full network integration are required. Its lack of RADIUS support, limited device compatibility, and short certificate lifetimes create unnecessary challenges for IT teams managing modern, hybrid environments.
Foxpass is the best alternative. It delivers all the benefits of certificate-based security, without locking you into a single platform. With certificate-based authentication, seamless identity integration, and a fully managed Cloud RADIUS backend, Foxpass makes it easy to implement secure access policies across any device, user, or location.
Whether you're looking to replace Microsoft Cloud PKI or extend its capabilities, Foxpass gives you everything you need in a single, easy-to-manage platform.
Start your free trial of Foxpass today and see how effortless secure access can be.