Introduction & Background
Certificate-based authentication (CBA) is one of the strongest ways to protect access to Microsoft 365, Azure portal, and other Entra-protected applications. Many organizations want CBA benefits, such as phishing-resistant authentication, password elimination, and strong device identity, but don’t want to operate a certificate authority or pay additional for Microsoft Cloud PKI.
Foxpass Cloud PKI offers a fully managed private PKI that works across all device platforms and integrates cleanly with Entra ID to enable CBA with minimal overhead. This guide gives you a walkthrough of:
The architecture for Entra CBA using Foxpass Cloud PKI
How Foxpass Cloud PKI issues ClientAuth certificates
How to deploy certificates using your MDM
How to set up Entra CBA
How to use the same certificate for Wi-Fi/VPN with Foxpass Cloud RADIUS
Follow this guide, and you’ll soon have a working CBA deployment using Foxpass as your private PKI.
Reference Architecture for Entra CBA with Foxpass Cloud PKI
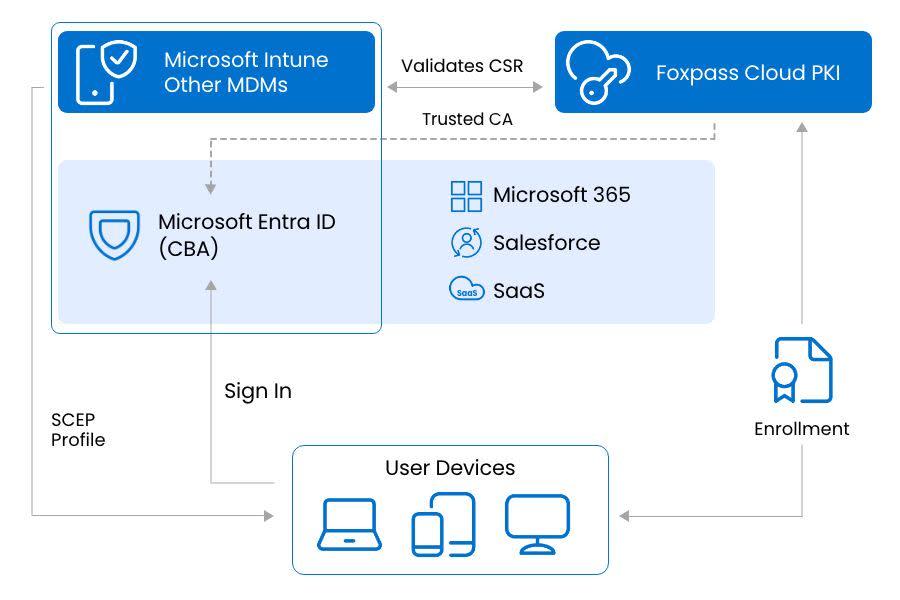
A diagram showing how Foxpass Cloud PKI, MDM, and Microsoft Entra ID work together for certificate-based authentication.
Foxpass Cloud PKI issues Client Authentication certificates to devices via the organization’s MDM (such as Intune, Jamf, Iru/Kandji, or Addigy). Devices present these certificates when signing into Microsoft Entra ID using CBA. Entra validates the certificate chain, user mapping, and EKU before granting access to cloud apps.
Prerequisites & Requirements
Foxpass Requirements Checklist
Foxpass Cloud PKI enabled
Client CA created and exported
SCEP endpoint created
MDM integration and/or BYOD installer
Microsoft Entra Requirements Checklist
Entra ID tenant
Certificate-Based Authentication enabled
Client CA from Foxpass uploaded
SAN (UPN/email) mapping defined
MDM Requirements Checklist
SCEP profile capability
Step-by-Step Configuration Guide
1. Verify or Create Your Client CA in Foxpass
Foxpass Cloud PKI requires a Client CA (issuing certificate authority) to sign device certificates used for Microsoft Entra CBA and EAP-TLS Wi-Fi/VPN.
Log in to the Foxpass Console and go to RADIUS → EAP-TLS
If no Client CA exists yet, create one now:
Under "Client Certificate Authorities," click "Create new Client CA"
Edit the CA Name, CA Validity, and Certificate Validity Period if desired, then click "Create CA"
3. Under "Client Certificate Authorities," click "Download CA" to save for later
Once the client CA is created, Foxpass automatically issues client Authentication (ClientAuth) EKU certificates, certificates with proper Key Usage extensions, and SAN/Subject values sourced from your MDM enrollment.
2. Ensure a Foxpass SCEP Endpoint Exists
All supported MDMs use SCEP to request and renew certificates from Foxpass.
Go to Foxpass Console → RADIUS → SCEP
If a SCEP Server URL (Unique Endpoint) is already shown, proceed to step 4
Click "Create SCEP Endpoint" then designate a Name, Verification Type, Authentication Type, and select the Client CA from Step 1 earlier
Note the "Unique Endpoint" and "Challenge Password" for later
3. Deploy Certificates Through Your MDM or Foxpass BYOD Certificate Installer
Once the Client CA and SCEP endpoint are in place, your MDM can issue device certificates for Entra CBA.
Foxpass supports SCEP-capable MDMs (Microsoft Intune, Jamf, Iru (Kandji), Addigy, and more), as well as the Foxpass BYOD Certificate Installer (OAuth-based enrollment).
Your MDM determines the Subject/SAN (UPN or email), renewal behavior, and key generation. Foxpass signs the certificate and handles revocation.
Option A: Microsoft Intune
Step A1: Create a SCEP certificate profile
Go to Intune Admin Center
Navigate to Devices → Configuration profiles → Create profile
Choose platform (Windows, iOS/iPadOS, macOS, Android)
Profile type: SCEP certificate
Set the following key settings:
Setting | Value |
SCEP Server URL | Foxpass SCEP ‘Unique Endpoint’ |
Subject name format | {{UserPrincipalName}} or {{EmailAddress}} |
Key size | 2048 or 4096 |
Key usage | Digital Signature, Key Encipherment |
EKU | Client Authentication |
Hash algorithm | SHA-256 |
Renewal threshold | Recommended 20–30% |
Step A2: Configure SCEP Authentication
Authentication type → Shared Secret
Secret → Foxpass SCEP "Challenge Password" (from Foxpass Console)
Step A3: Assign & Validate
Assign profile to user/device groups and verify:
Certificate issued by Foxpass Client CA
SAN/Subject matches UPN or email
EKU = Client Authentication
Option B: Jamf / Iru (Kandji) / Addigy / Workspace ONE / Mosyle
Entra CBA does not require Intune for certificate provisioning. This means you can use Entra CBA even in environments not managed by Intune, including mixed Apple fleets, cross-platform deployments, EDU environments, contractor/BYOD devices, and organizations using non-Microsoft MDMs.
These MDMs follow the same underlying logic as Intune, using SCEP to generate keys on-device and request certificates from Foxpass. You can find complete instructions for each here:
Option C: BYOD Devices
Use the Foxpass BYOD Certificate Installer and complete the following steps:
User signs in using OAuth with Microsoft Entra ID (Note: the BYOD installer’s Google sign-in cannot be used for Microsoft Entra CBA. CBA requires certificates that map to Entra identities.)
Foxpass issues a ClientAuth certificate
Certificate installs locally (no MDM required)
This is ideal for contractors, student devices (EDU), or unmanaged endpoints.
4. Upload the Foxpass Client CA to Microsoft Entra
To use this method, Microsoft Entra must trust your issuing CA.
Step 1: Download the Client CA certificate
Go to Foxpass Console → RADIUS → EAP-TLS
Download the Client CA certificate
Step 2: Upload the Client CA to Entra
Go to Entra Admin Center → Protection → Certificate-Based Authentication → Certificate Authorities
Upload the Foxpass Client CA certificate
5. Configure Microsoft Entra Certificate-Based Authentication
In Entra Admin Center:
Enable Certificate-Based Authentication
Choose mapping rules:
SAN → UPN (recommended)
SAN → email
Required EKU → Client Authentication
Optional: Restrict by issuer or certificate policy
Refer to Microsoft Learn for advanced mapping rules, EKU requirements, issuer constraints, and a full walkthrough of Entra CBA configuration:
https://learn.microsoft.com/en-us/entra/identity/authentication/how-to-certificate-based-authentication
6. Apply Conditional Access Policies
Create a Conditional Access policy:
Users: Start with a test group
Apps: Microsoft 365 or all cloud apps
Grant: Require Certificate-Based Authentication
Optional enhancements:
Block password-based login
Require compliant or domain-joined devices
Add MFA fallback
7. Test Certificate-Based Authentication
On a device with a Foxpass-issued certificate:
Enter your username
The browser prompts for a certificate
Select the Foxpass-issued certificate
Authentication succeeds without a password
If you experience any issue authenticating with a certificate, verify that the Issuer is Foxpass Client CA and the SAN/Subject matches the UPN/email.
(Optional) Use the Same Foxpass Certificate for Wi-Fi/VPN (EAP-TLS)
An advantage of using Foxpass Cloud PKI is that the same device certificate issued for Microsoft Entra CBA can also be used for secure Wi-Fi or VPN access via EAP-TLS with Foxpass Cloud RADIUS.
With EAP-TLS, organizations can:
Enforce Zero-Trust network access
Eliminate passwords for Wi-Fi and VPN
Ensure that only devices with a valid Foxpass-issued certificate may join
Apply VLAN assignment, device trust rules, or identity-based policies
Share the same certificate lifecycle across Entra CBA cloud authentication and network access
Conclusion
Using Foxpass Cloud PKI with Microsoft Entra CBA and your MDM gives you:
A fully managed private PKI
Cross-platform certificate issuance
Automated certificate lifecycle management
Unified certificate identity for SaaS access and Wi-Fi/VPN (optional)
Seamless integration with Intune, Jamf, Iru (Kandji), Addigy, and BYOD
This setup delivers a modern, passwordless, certificate-based approach for securing both identity and network access without running your own CA.