
Secure Server Access With Centralized SSH Key Management, Cloud-Linked Authentication, and Group-Based Sudo Access Control
Automate SSH key distribution, enforce least privilege, and simplify user offboarding — all synced with your organization's cloud IdP (Entra ID, Google Workspace, Okta, or OneLogin).

The Challenge
Managing SSH keys and local user accounts across engineering environments quickly becomes complex and insecure. Teams struggle to:
Track which users have SSH access to which systems
Remove access immediately when employees or contractors leave
Rotate SSH keys and passwords regularly
Enforce consistent sudo privileges
Prove access control compliance for SOC 2, ISO 27001, or internal audits
Without central management, orphaned keys and unmanaged sudoers files create real risk — and real operational drag.
The Foxpass Solution
Foxpass simplifies secure access to Linux, macOS, and UNIX systems by centralizing:
SSH public key storage and rotation
POSIX user and group definitions (UID, GID, shell)
Password-based login via LDAP
Sudo access tied to directory groups
All integrated with your identity provider (Google, Okta, Entra ID, OneLogin) and enforced via your existing infrastructure. No new agents or servers required.
What You Can Do with Foxpass
![A blue outline of a key inside a blue square border on a white background, representing a symbol for access or security.]()
SSH Key Management
Upload, revoke, and rotate keys from the Foxpass console or API
Enforce key-based login only (no password fallback)
Automatically sync keys to LDAP-backed servers
Ensure keys are removed instantly on offboarding
![Blue icon of a computer monitor displaying a password entry field with three dots and a dash, symbolizing password protection or login on a digital device.]()
LDAP-Backed Password Login
Use directory credentials to authenticate to Linux/macOS
Set POSIX fields like UID, shell, and home directory
Enforce password complexity and expiration policies centrally
![Blue icon of a person standing next to a large key on a light background, symbolizing user access or account security.]()
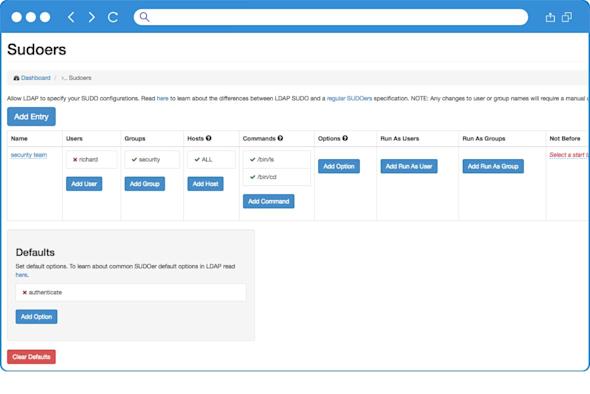
Sudo Access Enforcement
Define sudo access based on LDAP group membership
Dynamically grant/restrict privilege escalation
Replace static sudoers files with directory-driven control
![A blue icon showing a padlock, a left-pointing arrow, and a speech bubble, symbolizing secure messaging or protected communication.]()
Audit and Compliance
Track login attempts and sudo usage
Export logs for audit reporting (extendable to 90 days)
Ensure compliance with SOC 2, HIPAA, internal security policies

Common Scenarios
Rotate developer SSH keys every 90 days
Grant temporary sudo access to a contractor
Lock down SSH access for a new production server
Prove access policy enforcement during a compliance audit
Tie Linux/macOS access to Okta or Google group membership
Achieve zero-trust server access with automated SSH key and identity management. Replace static credentials with dynamic SSH key rotation and group-based access policies — integrated with your cloud IdP for complete visibility and control.
How to Enable This Capability
SSH Key & Password Management is available through the Foxpass Engineering License Add-On, which extends your existing Foxpass LDAP directory with:
POSIX attributes
SSH key controls
Sudo group policies
Full Linux/macOS login enforcement
Ready to Modernize Your SSH Access Controls?
Say goodbye to manual key management and scattered login policies. Foxpass gives your team secure, scalable access control that aligns with zero-trust best practices.



