There’s a tricky balance between security and convenience. If you make authentication too easy, hackers and other bad actors can sneak through, but if it’s too complex, you’ll lose out on productivity and drive employees mad. Secure Shell (SSH) keys help strike that balance, providing secure authentication for automated processes and implementing single sign-on.
With that in mind, let’s explore SSH keys, how they’re used, and how Foxpass provides accessible, user-friendly SSH key management...
What is an SSH Key?
An SSH key is an alternative to usernames and passwords as a method of user authentication. It is primarily used by presenting an encrypted file to the service instead of a text-based password.
Access credentials for SSH keys are exchanged in the Secure Shell protocol, a secure alternative for the unencrypted Telnet. SSH keys use cryptographic techniques to ensure that all communication to and from the remote server happens in an encrypted manner.
This provides a secure mechanism for authenticating remote users, transferring input from the client to the host, and relaying the output back to the client.
In practice, each user generates their own SSH key pair, keeping the private half on their machine and installing the public half on servers they need access to.
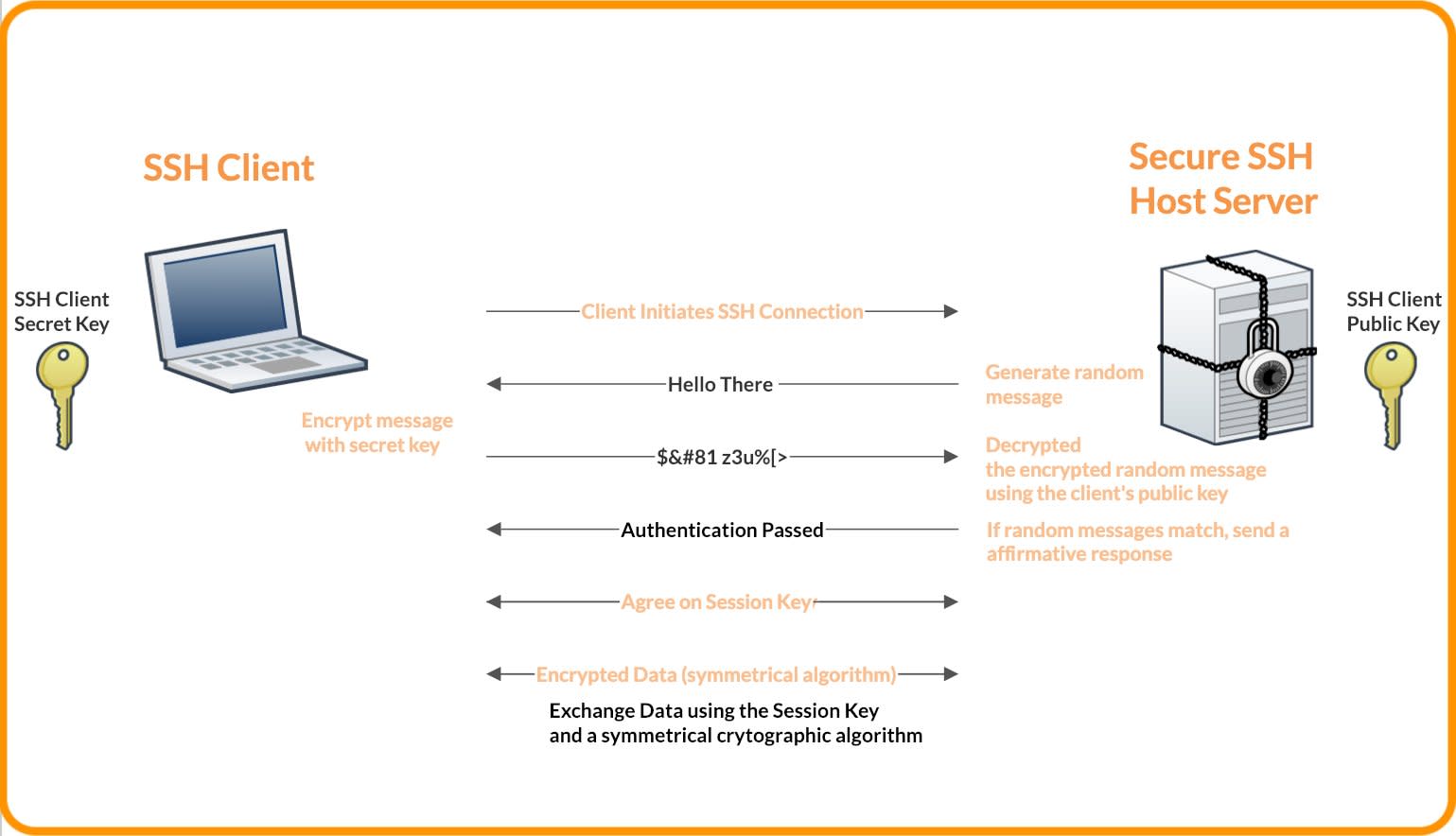
How are SSH Keys Used?
SSH keys are similar to passwords, as they grant access to users and help authenticate their identities, determining who can access what systems. SSH keys establish secure connections that encrypt data, allowing users to securely log in and work without fear of anything being intercepted.
As a result, SSH provides high security and confidentiality when logging in (even remotely), sending data, and transferring files.
SSH keys are primarily used to log into Linux servers. These servers work behind the scenes to power most websites and apps.
Software engineers need to continually log into these servers to deploy code, fix bugs, and configure settings. SSH keys enable them to easily access the servers without having to constantly log in and out while maintaining authentication, ensuring efficiency and security.
SSH Key Management
However, SSH keys can present a new challenge, as managing a massive number of keys can be a tricky process. When companies fail to implement provisioning and termination processes for key-based access or have no records for who provisioned keys for what, that can introduce new security risks.
SSH key management, therefore, is vital for ensuring security when provisioning SSH keys. SSH key management includes:
Managing identities and credentials
Provisioning and terminating SSH keys
Implementing privileged access management
Having incident response and disaster recovery plans in place
With proper SSH key management, you can ensure users quickly receive the keys and credentials they need to work, manage who has access to what, and remove credentials when they’re no longer needed, thus keeping your systems secure.
Why Foxpass is a Great Manual SSH Key Management Alternative
If you need a powerful solution to help with SSH key management, Foxpass offers the easiest and most secure way to manage your SSH keys and keep your servers secure. Foxpass’s SSH key management feature lets engineers add their public keys to Foxpass, so they can log into Foxpass-enabled Linux machines from their own computers, enabling self-service SSH key management.
Additionally, Foxpass provides several features designed to make SSH key management easy, like temporary access and pattern-based host matching. This provides efficient and secure access management and control, working seamlessly with your SSH keys.
This is just one of the many ways Foxpass offers enterprise-grade security at an affordable, approachable price. With Foxpass, you can keep your networks and devices secure without compromising speed and efficiency.
Upgrade Your Security
Want to help your employes securely and easily connect to your network while keeping bad actors at bay? Click here to learn how Foxpass can help you avoid costly security mistakes:




