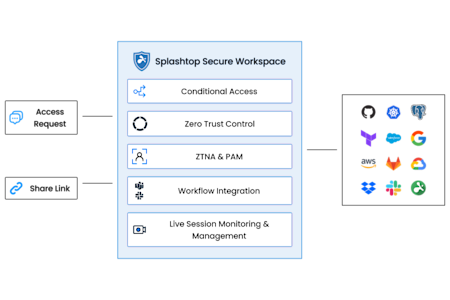
Secure Third‑Party Access
Flexible and fast onboarding and off-boarding of temporary workers, contractors, and vendors.

Agent-less Access
Enables third-party users to connect to applications, resources, or endpoints without installing additional software.
Supports popular protocols like RDP, SSH, and web applications, making access seamless and device-independent.

Just-In-Time (JIT) Access
Enables secure, time-bound access to specific resources through sharable links without sharing admin credentials, reducing risks of credential theft.
Enforces least privilege, adheres to security policies, and automatically revokes access after expiration to minimize risk.

On-Demand Access
Integrates with collaboration tools like Microsoft Teams and Slack to streamline Access Requests.
Notifies individuals or channels in real time, allowing administrators or managers to approve or deny requests directly within these platforms.

Granular Access Control
Offers policy-driven access to specific resources, ensuring that third-party users only access what is necessary.
Implements the least privilege principle, reducing security risks associated with broad access.

Session Monitoring and Recording
Provides real-time monitoring, termination, and recording of user activities during remote sessions, enhancing visibility and accountability.
Enables secure playback for troubleshooting, security analysis, or training.

Remote Browser Isolation (RBI)
Ensures secure browsing for third-party users accessing SaaS applications or sensitive internal resources, preventing data leaks and unauthorized access.
Isolates browser sessions to protect against malware, phishing, and other web-based threats, safeguarding sensitive organizational data.
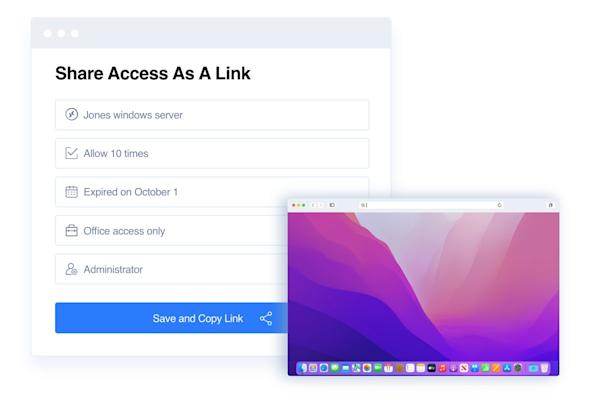
Application "Just-In-Time" Share Link
Give access through an easy-to-use secure link.
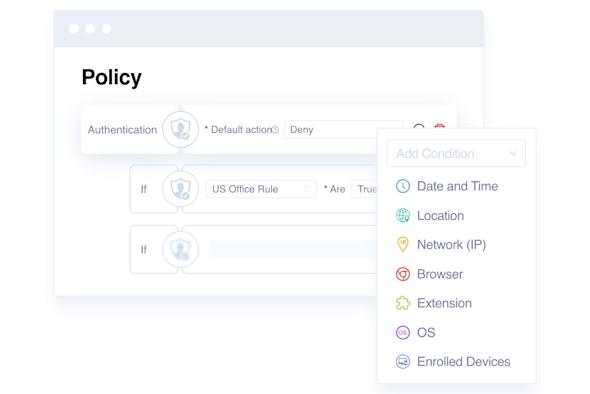
Conditional Access
Setup policies for conditional access based on time, location, device posture, and more!

Securing Third-Party Access: Splashtop's Just-In-Time Approach
In the world of IT, the necessity for third-party access is undeniable, yet it introduces cybersecurity risks that cannot be dismissed.

How to Simplify Secure Access for Third-Parties and Temporary Users
In today’s interconnected business environment, collaboration with external parties such as vendors, contractors, partners, and suppliers is the norm.

Mastering Web App Security with Splashtop Secure Workspace
Today, organizations increasingly conduct work remotely, move towards cloud-based systems, and collaborate with outside contractors through the course of business.

Tutorial Video: Temporary Access Sharing & Session Control
This video is an overview of the Secure Workspace's secure access and share control.

Tutorial Video: Agentless and BYOD Access
This video is an overview of the Secure Workspace Web Portal and shows how IT Managers can use this all-in-one application launcher to launch an RDP and VNC application.
