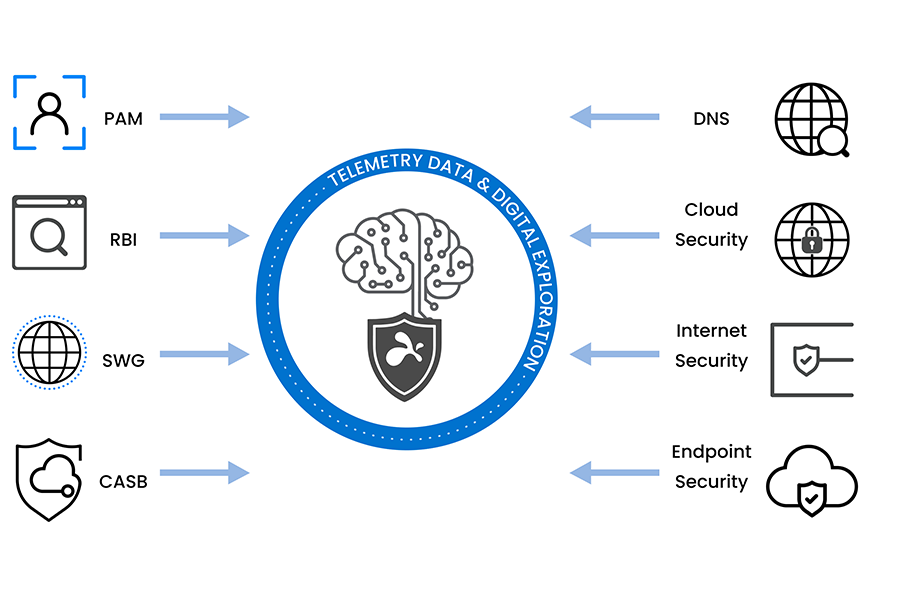
Comprehensive Telemetry Data and Monitoring
Manage identity, applications, and endpoints holistically, offering full visibility and security telemetry analytics for security operations.

Security Telemetry
Centralized security telemetry analytics from various IT infrastructure sources to monitor for suspicious activities, vulnerabilities, potential breaches or digital experiences:
Network data
Log Data
Endpoint data
Trace data
User behavior data
Application data
Realtime Session Management
Streamlined Network Control: View and terminate network sessions for efficient infrastructure management.
Secure Vault Access: Precisely manage secret vault sessions to ensure sensitive data remains protected.
Advanced Application Session Management: Employ shadowing for live monitoring, record sessions for in-depth audit, and terminate risky actions instantly to bolster security.
Telemetry & Digital Experiences Dashboards
The dashboard provides global visibility and a live view of activities within your digital workspace. It features immersive charts to help fine-tune your policy configurations, including:
Organization Overview
Network & Application
Endpoint Devices
Privileged Access
Internet Access
Secret Vault Security Posture
