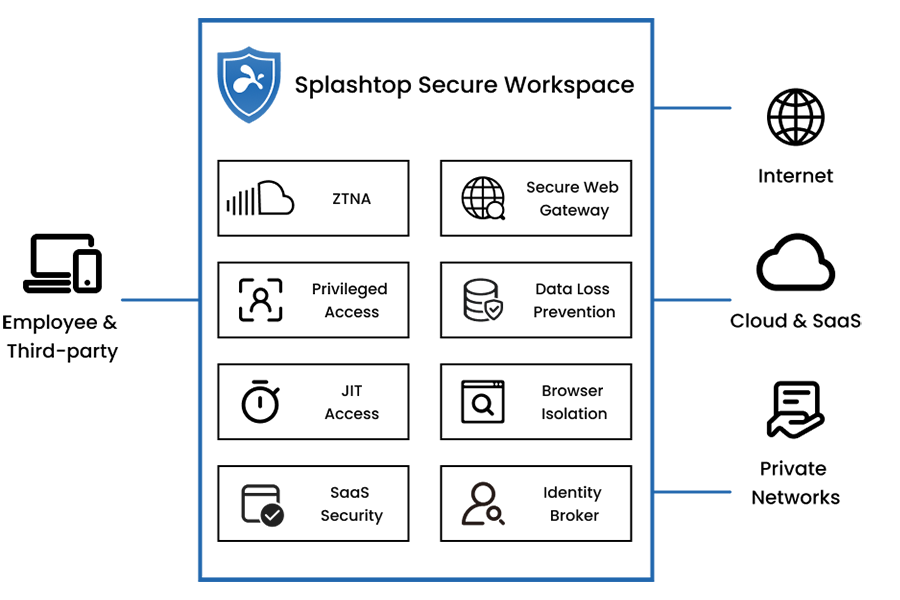
Zero Trust semplificato
Piattaforma di accesso sicuro unificata con servizi SSE e SASE






Manda in pensione la tua VPN e scegli l'accesso di rete Zero Trust di nuova generazione (ZTNA)
Applica criteri zero-trust e default-deny per gli utenti che accedono alle tue risorse interne. Questo approccio è più veloce e sicuro di una VPN, in quanto impedisce i movimenti laterali e il backhauling del traffico.
Accesso sicuro di terze parti con registrazione delle sessioni e monitoraggio in tempo reale
Potente accesso Just-in-Time (JIT), senza credenziali e limitato nel tempo, con la Gestione remota degli accessi privilegiati (RPAM). Protezione dalle minacce di Internet e dalla perdita di dati con Remote Browser Isolation (RBI). Supporto per BYOD, accesso clientless e dispositivi non gestiti, per ambienti IT e OT.
Sicurezza Zero Trust di nuova generazione
![Blue outline icon of a computer monitor with a triangular warning sign containing an exclamation mark in front, suggesting a computer or display error or alert.]()
Rete Zero Trust
Alternativa più sicura e veloce alle VPN legacy con microsegmentazione, riducendo i movimenti laterali.
![Blue outline icon of an ID card with a user silhouette and horizontal lines, accompanied by a large check mark in a circle, indicating verification or approval.]()
Accesso con privilegio minimo
L'accesso sicuro Zero Trust permette di accedere solo a ciò che è necessario in base all'identità, al ruolo, al dispositivo e al contesto di rete.
![Blue outline icon of a computer monitor with a video camera symbol in the top right corner, suggesting video calling or video conferencing.]()
Monitoraggio delle sessioni in tempo reale
Le sessioni remote sono monitorate, controllate e registrate, fornendo piena visibilità sulle attività degli utenti.
Facilità d'uso
![A blue line forms a square on the left, then curves upward into a large arrow pointing diagonally to the top right on a light gray background.]()
Facilità di implementazione
Niente più complesse gestioni delle policy VPN. L'accesso sicuro e la connettività possono essere configurati in pochi minuti.
![A blue outline of a clock showing 3 o’clock, with bold hour markers at 12, 1, 2, and 3, on a light gray background.]()
Accesso just-in-time
Gli utenti ottengono l'accesso temporaneo alle risorse solo quando necessario, con un tempo limitato e autorizzazioni precise.
![Blue outline icon of an open laptop connected to a network node below, symbolizing a computer linked to a network. The background is light gray.]()
Accesso ZTNA agentless
L'accesso ZTNA agentless elimina la necessità di installare il software e consente l'onboarding rapido di fornitori di terze parti e utenti BYOD.

Trasformare l'accesso sicuro con Splashtop Secure Workspace
Yanlin Wang, VP of Advanced Technology, spiega come rompere gli schemi di sicurezza per consentire l'accesso sicuro alle risorse ovunque e in qualsiasi momento.

La gestione dell'identità e dell'accesso spiegata: Guida completa all'IAM
Nel panorama digitale in rapida evoluzione, la necessità di proteggere i dati sensibili e gestire l'accesso degli utenti in modo efficace non è mai stata così critica.

Come mitigare l'attacco XZ Backdoor Supply Chain
Nell'era digitale, gli attacchi alla supply chain sono emersi come un sofisticato vettore di minacce, in quanto sfruttano l'interconnessione dei moderni ecosistemi software.

Garantire l'accesso di terze parti: l'approccio just-in-time di Splashtop
Nel mondo dell'IT, la necessità di concedere l'accesso a terze parti è innegabile, ma introduce rischi per la sicurezza informatica che non possono essere ignorati.






