How Your Remote Team Can Address the Rise of Cyberattacks
Share This
Once again, and for the 18th consecutive October, it is Cybersecurity Awareness Month. Top of mind for the Cybersecurity & Infrastructure Security Agency (CISA) this year is the security of remote work architectures and remote workers. In 2020, Organizations made a rapid pivot to fully remote work, and many plan to continue with either full or partial remote workforces on a permanent basis. This quick shift to remote work has left organizations vulnerable to an expanded threat landscape of cyberattacks.
How expanded and varied are cyberattacks?
Just consider a couple 2021 insights by leading cybersecurity resources. Norton recently published an article, 115 cybersecurity statistics and trends you need to know in 2021—that’s 115! At the same time, Verizon’s 2021 Data Breach Investigations Report provides 119 pages of data and commentary around a range of cyberattack incident types, including the 20 most common, nefarious actions that criminals took when breaching organizations in 2021. Verizon alone had confirmed and analyzed a full 5,258 data breaches as of the report’s September 2021 publication date. Company leaders must take defensive steps to protect their organizations from these increasing threats.
The security burden is for all to share
It’s important to note that an organization’s vulnerability to cyberattacks relates to both people and IT infrastructure. For that reason, a security approach to your remote work environment must account for the most common people-related risk factors as well as IT infrastructure risk factors.
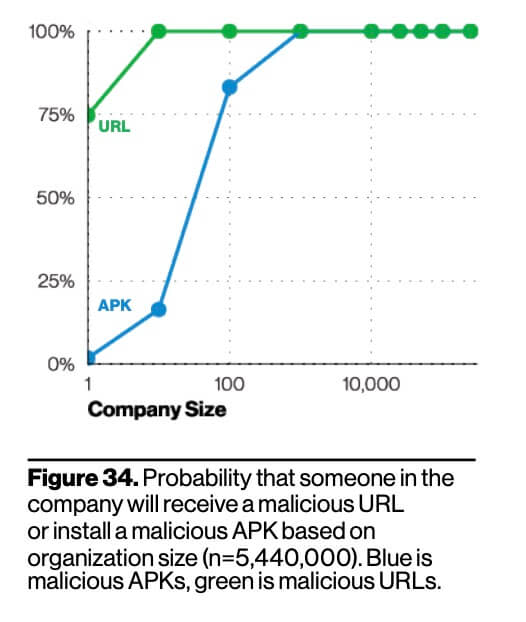
People-related risk factors
As you are likely aware, the weakest link in any organization’s security defense is usually the end-user. Most breaches are caused by a simple error, such as an employee clicking on a harmful link, saving a corrupted file, using a weak password, or forwarding harmful things to others. In fact, according to the Verizon study, there is a 100% chance that your people will be targeted if your organization has 100 or more employees.
In light of this, there are two major steps leaders should take to make employees more vigilant:
Step 1: Have executives promote end-user awareness training
When a C-level executive pushes people to undertake training, it gets done. Have your executives send messages that emphasize the importance of security and stress that it’s everyone’s responsibility. CISA published a couple of great resources that can help reinforce your remote work-specific security training:
Step 2: Establish living security policies
Many companies have security policies. However, to make them truly effective and ensure that people adhere to them, you must continuously monitor, test, and enforce them.
It’s important to note that few data breach incidents are caused by employees who ‘go rogue.’ Still, you cannot tell who has been compromised. That’s why top-performing companies and security leaders are adopting stronger security architectures, wherein users can only gain access to apps, data, and other resources by continuously verifying credentials. Even when they do, users can only access the areas for which they have personalized permissions.
IT-related risk factors
Needless to say, when it comes to cybersecurity, there is an endless stream of solutions and advice to help you secure your IT environment. Fortunately, CISA has assembled a focused set of valuable resources, the Telework Reference Materials for Non-Federal Organizations. These resources were developed in collaboration with leading IT security solution vendors and industry experts. They cover a wide range of remote work-specific IT recommendations – 26 to be exact.
VPNs can leave you vulnerable to cyberattack
People who work remotely typically use VPNs and remote desktop protocol (RDP) to access the apps and data they need to perform their work. This has led cybercriminals to exploit weak password security and VPN vulnerabilities to access the corporate network, steal information and data, and worst of all – inject ransomware.
According to Reuters, the April 2021 hack of the Colonial Pipeline that froze oil supply to the U.S. southeast was the result of a VPN break-in. The break-in likely could have been avoided if pipeline leaders had protected the VPN with multi-factor authentication. The organization was fortunate to escape with just a $5 million Bitcoin payment but will likely face long-term scrutiny and brand damage.
Relying on VPN access is a losing proposition when defending against modern cyberattacks. With VPN technology being decades old, it simply cannot be secured the way modern access solutions – especially cloud-based access can be. Not to mention, a VPN’s success depends on your IT department correctly configuring it. VPNs are often exploited because there’s no standard way to set them up or distribute access.
Remote access can help with remote work security challenges
A remote access solution mitigates the risks inherent in VPNs, because it enables you to restrict employee streaming to just their desktops. This means the data in your corporate network is protected. Employees working remotely can edit a file if they have been granted permission, otherwise they can only view the data. Those with viewer-only access cannot modify, manipulate, or even download it. This stands in sharp contrast to VPN-based access that allows any credentialed user to download data at will.
Advanced remote access solutions introduce even more security features, such as device authentication, two-factor authentication (2FA), single sign-on (SSO) and more to keep you and your organization safe.
“While there is a learning curve as people adopt remote access solutions, you can minimize that with the right partner. Since Splashtop was designed originally for the consumer market, the time it takes to learn it is minimal. And by minimal, I mean within a few minutes for the average user.” - Jerry Hsieh, Senior Director of Security and Compliance at Splashtop
Conclusion: it takes a village
With people working remotely, the threat landscape growing broader, and cyberattacks happening more frequently, organizations must take a holistic approach to address the emerging cybersecurity threats of 2021. This means hardening the defensive posture of both your people and your IT architecture.
The good news is that you can make very pragmatic changes in just a few areas to achieve a substantial leap forward in protection against cyberattacks. In addition, it has become clear that both the U.S. Government and security industry leaders have doubled their efforts to both enable and advise organizations like yours to operate safe and secure remote work environments.
At Splashtop, we’re proud to deliver an essential element of secure remote work. Learn more about Splashtop's Remote Access Security Features.
Additional Resources
Discussing Security, Ransomware and What Security Teams Should Be Thinking About with Jerry Hsieh
Cyber-Attacks Infographic: What You Should Know and Tips for Prevention
Leaders in Cyber Security: Q&A with Mark Lee and Sramana Mitra
Is Next-Gen Remote Access Software the Solution to Insecure RDP?
To keep up-to-date with the latest cybersecurity news, subscribe to our Security Feed.
To learn more about Splashtop’s remote access and remote support solutions, visit our Product Page.